The notorious conti blackmail Gang announced that it had officially stopped operation, its infrastructure had been offline, and the gang leaders announced that the brand no longer existed The news comes from yelisey boguslavskiy of advanced Intel. He tweeted today that the internal infrastructure of the gang has been shut down.

Although the "conti news" data leakage and ransom negotiation website for the public is still online, boguslavskiy told bleepingcomputer that the tor management panel used by members to carry out negotiations and publish "news" on their data leakage website has now been closed. In addition, bleepingcomputer was informed that other internal services, such as their rocket chat server, were being retired.
Recently, Costa Rica announced a "war" against conti, but at present, the relevant activities have not been fully carried out, so it is a little strange to close now. Boguslavskiy revealed that conti's public attack was to set a flag and raise awareness, while conti's members gradually moved to smaller extortion software operations.
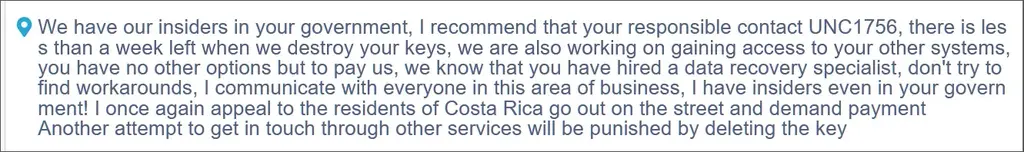
A report released by advanced Intel said: "however, the unique confrontational visibility and intelligence discovery of advanced Intel lead to the opposite conclusion. The only purpose conti wants to achieve through this final attack is to use this platform as a publicity tool to deduce their own death and subsequent rebirth in the most reasonable way".
The report continued: "this large-scale attack was only to publicize its strength, not for ransom, which was also confirmed within conti's leadership. Internal communication among members of the organization showed that the ransom requested was far less than $1 million (although the unverified ransom claimed to be $10 million, and conti later claimed that the amount was $20 million).
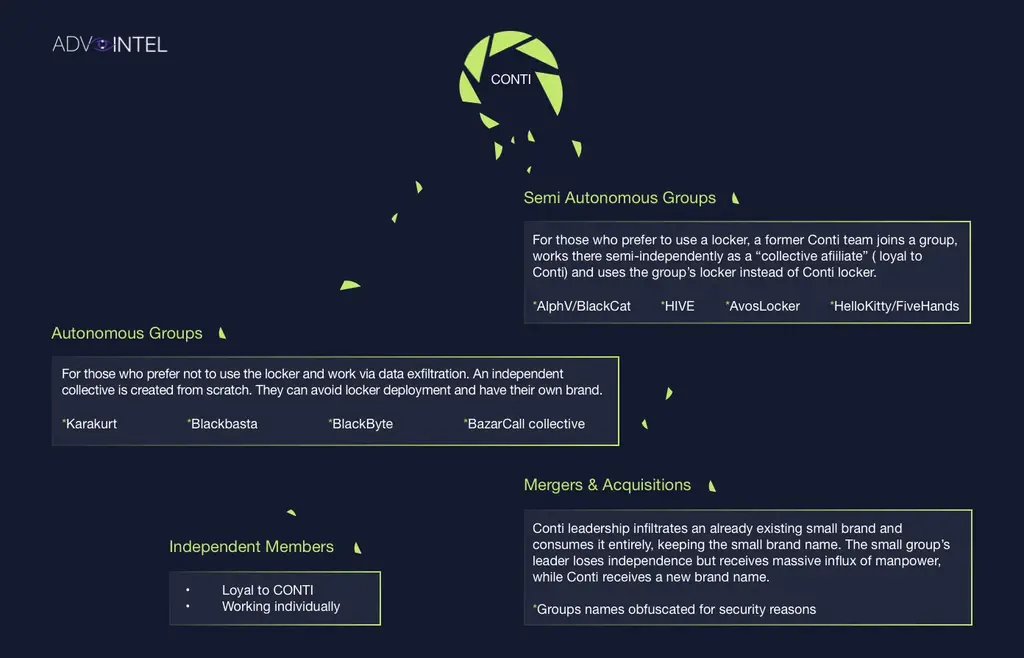
Although conti blackmail software brand no longer exists, the cybercrime group will continue to be active in the blackmail software industry for a long time in the future. Boguslavskiy told bleeping computer that conti's leadership did not recreate another large-scale extortion software operation, but cooperated with other small extortion software gangs to attack.
Under this partnership, smaller extortion software gangs have obtained a large number of experienced conti five person groups, negotiation experts and operators. The conti cybercrime group has gained mobility and greater evasion of law enforcement by splitting into smaller "groups", which are managed by the central leadership.
The senior Intel report explained that conti has cooperated with many well-known blackmail software actions, including hellokitty, avoslocker, hive, Blackcat, blackbyte, etc.