Over the past few years, the threat of ransomware has been growing. Although most of them are aimed at a wide range of attack surfaces and contain opportunistic attack modes, Microsoft has now issued a warning about human operated ransomware (we call it "hor" for brevity), which is becoming dominant in the economy of ransomware as a service (RAAS).
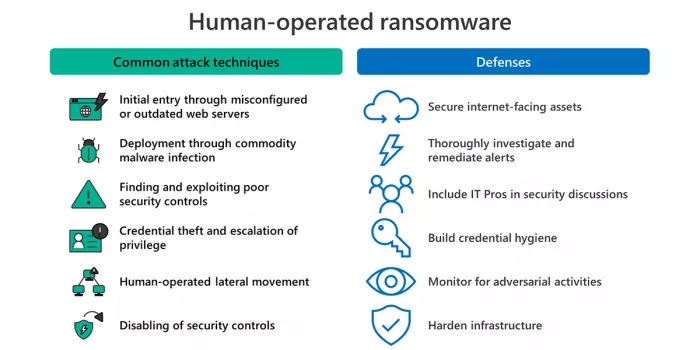
Hor is different from traditional blackmail software because it aims at specific weaknesses in specific systems and is manually discovered by humans. An example is the use of services with high permissions in the environment. Microsoft said that hor has human input at each stage of the attack. System defects or human errors may be used to improve permissions, obtain more sensitive data, and eventually bring greater compensation power. What makes hor more dangerous is that attackers usually don't leave the victim's network after payment. They constantly try to make their access continue to generate harm and revenue by deploying new malware until they are completely eliminated.
Microsoft stressed that RAAS recently began to tend to the dual blackmail mode. The victim's data is not only encrypted, but also the attacker threatens to make it public until he receives the money. The company also pointed out that hor activities usually use traditional configuration and wrong configuration, as well as poor credential status to improve their authority. Therefore, security experts in enterprises need to transition to zero trust mode. They should not only pay attention to a single alarm, but also have an overall view of the whole security situation and events.
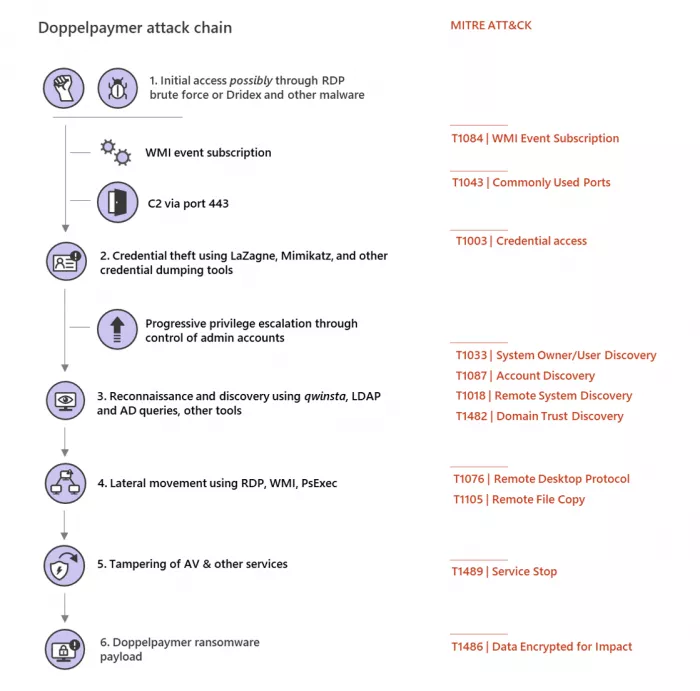
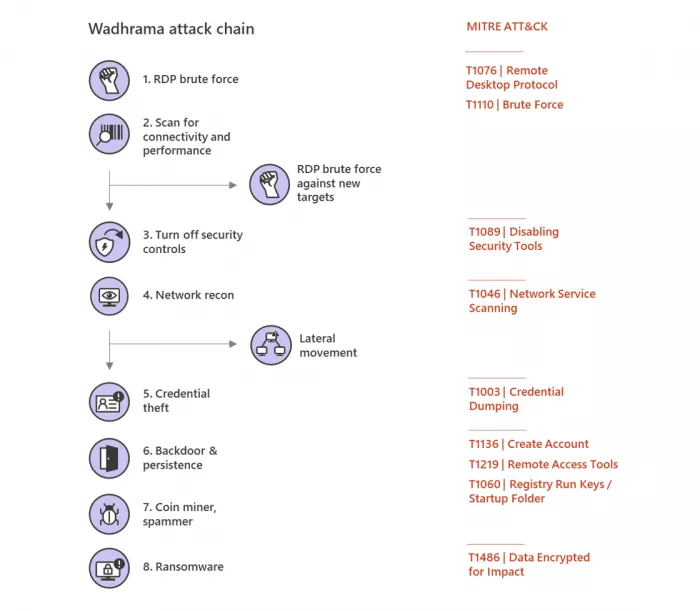
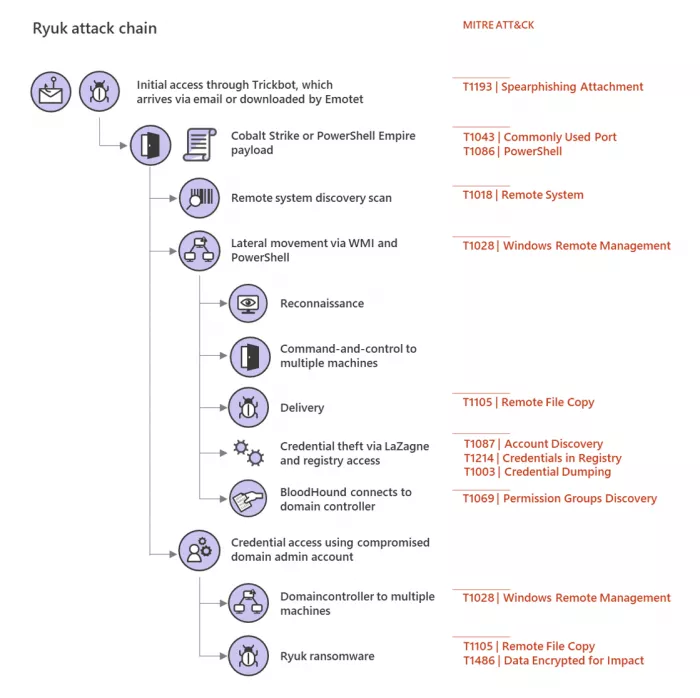
Microsoft also warned organizations about the existence and development of the RAAS alliance model, as follows:
In the past, we have observed that in each activity of a ransomware, there is a close relationship between the initial entry carrier, tools and the payload selection of the ransomware. The RAAS alliance model allows more criminals, regardless of their technical expertise, to deploy extortion software built / managed by others, which weakens this connection. As the deployment of ransomware becomes a part-time economy, it becomes more difficult to connect the technology used in specific attacks with the payload developers of ransomware.
[RAAS is an arrangement between operators and affiliates. RAAS operators develop and maintain tools to support the operation of ransomware, including builders for the production of ransomware payloads and payment portals to communicate with victims.
[... ] therefore, RAAS gives a unified feeling that the payload or activity is a single family of ransomware or a group of attackers. However, what happened was that the RAAS operator sold the ransom payload and access to the decryptor to an affiliate that performed intrusion and privilege upgrades and was responsible for deploying the actual ransom software payload. Then the two sides share the profits. In addition, RAAS developers and operators may also use payloads for profit, sell them, and carry out activities together with other ransomware payloads - making it more difficult to track the criminals behind these actions.
In order to combat these growing complex threats, Microsoft suggests that enterprises should move to the zero trust mode, establish credential hygiene, audit credential exposure, implement cloud reinforcement, give priority to the deployment of active directory updates, reduce the attack surface, alleviate the security blind spot, and strengthen the surrounding environment, especially Internet Oriented resources. Use the unified investigation function and cross domain visibility of security software to detect and actively respond to threats.
Microsoft plans to discuss this field in more detail in the digital activity of Microsoft Security Summit on May 12. You can register here:
https://mssecuritysummit.eventcore.com/?ocid=AID3046765_QSG_584073