[Google announced today that the PSP (short for PSP security protocol) protocol is open source.] ( https://cloud.google.com/blog/products/identity-security/announcing-psp-security-protocol-is-now-open-source ) The protocol is designed to handle data center scale encryption hardware offloading. At present, the protocol has been deployed to Google's production.
In order to better protect users' privacy, Google encrypted the traffic between data centers more than a decade ago. In the subsequent development, almost all the data transmitted by Google were encrypted. Although this work provides valuable privacy and security advantages, software encryption pays a huge price: encrypting and decrypting RPC requires about 0.7% of Google processing power and the corresponding amount of memory.
These costs prompted Google to offload encryption to the network interface card (NIC) using PSP (short for PSP security protocol). The so-called offload is to put some packet processing (such as TCP segmentation, IP fragmentation, reorganization, checksum, TCP protocol processing, etc.) carried out by the operating system into the network card hardware to reduce the CPU consumption of the system and improve the processing performance.
In view of the unfriendliness of TLS, lack of support for UDP and some defects in IPSec, Google has independently developed its own offload friendly protocol. As their solution, PSP is described as a TLS like and transmission independent protocol for the security and offload friendliness of each connection.
For PSP, Amin Vahdat of Google cloud team explained
PSP is designed to meet the requirements of large-scale data center traffic. It does not require a specific key exchange protocol, and provides few choices for packet format and encryption algorithm. It achieves the security of each connection by allowing each layer 4 connection (such as TCP connection) to use an encryption key.
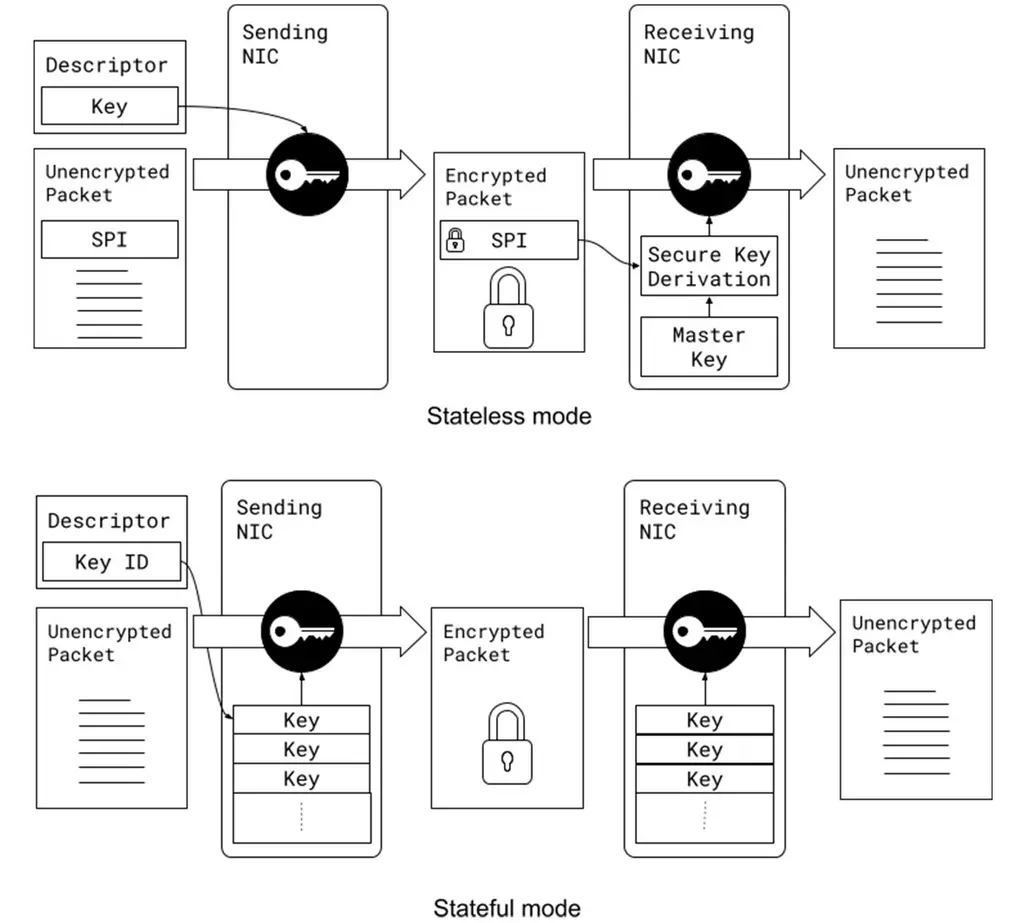
It supports stateless operation because the encrypted state can be passed to the device through the packet descriptor when transmitting the packet, and the packet can be received using the security parameter index (SPI) and the master key on the device. This enables us to keep the minimum state in the hardware, and avoids the hardware state explosion compared with the typical state encryption technology for maintaining large equipment tables.
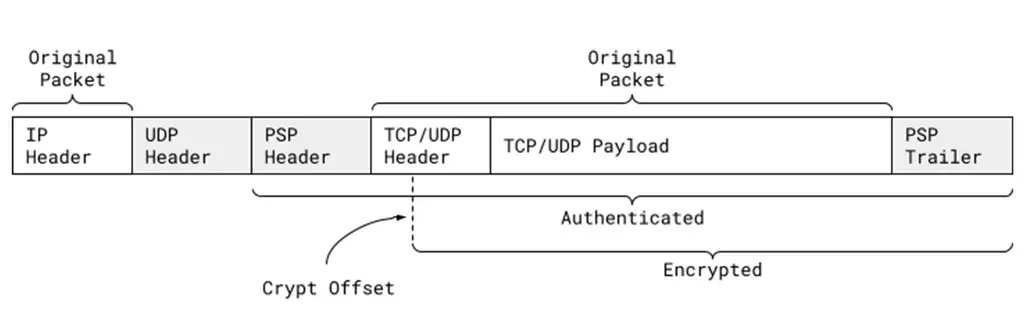
PSP is encapsulated by user datagram protocol (UDP) with custom header and trailer. A PSP packet starts with the original IP header, then the UDP header on the pre specified target port, then the PSP header containing PSP information, then the original TCP / UDP packet (including header and payload), and the Psp Trailer containing integrity checksum value (ICV).
Layer 4 packets (header and payload) can be encrypted or verified according to the offset called crypt offset provided by the user. For example, this field can be used to keep part of the TCP header authenticated but unencrypted during transmission, while keeping the rest of the packet encrypted to support packet sampling and checking in the network, if necessary.
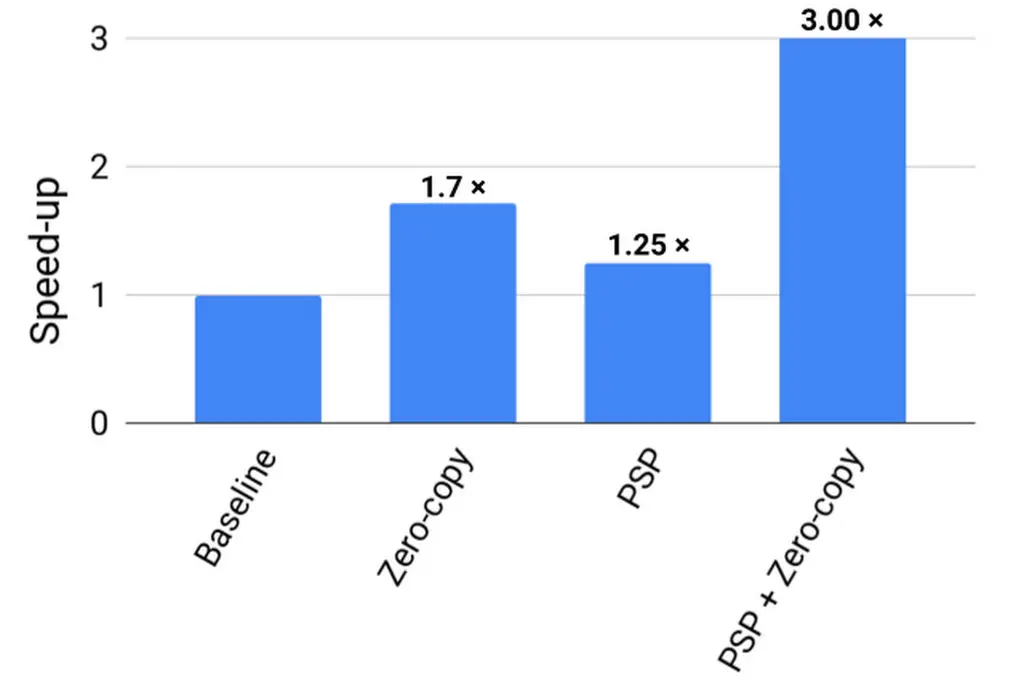
Google patched PSP into their production Linux kernel, their Andromeda network virtualization stack and their snap network system. It is reported that PSP encryption unloading can save about 0.5% of Google's overall processing power. Today, they open source the PSP security protocol to encourage its further adoption. They have released their architectural specifications, reference software implementations, and a set of test cases.