The annual pwn2own hacker conference is being held in Vancouver. By bringing together participants and network security experts, they can fully demonstrate the relevant Zero Day vulnerability exploitation and other software cracking methods, and obtain corresponding rewards and technical recognition In the first day report of pwn2own 2022, it can be seen that Microsoft Windows 11 operating system and teams team cooperation service have been broken by white hat contestants on the first day
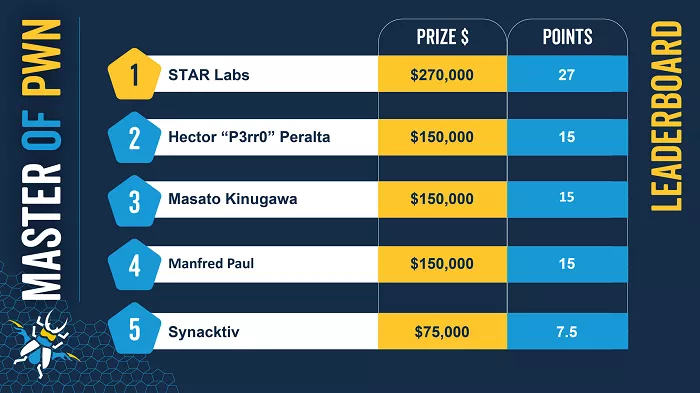
Pwn2own 2022 is also the 15th anniversary of this series of hacker conferences (figure from: zdi official website)
However, the next day, pwn2own's team still encountered some changes. For windows Of the two attack attempts of 11, only one demonstration was successfully achieved (the success rate was 50%).

Yueqi Chen, zdi analyst Tony fuller and Bobby Gould from Northwestern University's tutelary team.
Using improper configuration, the team was able to access windows 11 and achieve privilege enhancement (EOP), and received a $40000 bonus + 4 PWN Master points.
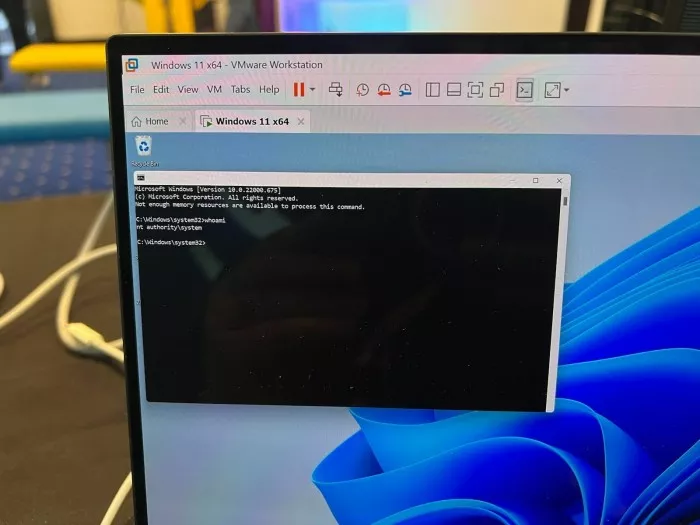
The viettel cyber security team exploited the integer overflow EOP vulnerability on Windows 11
Unfortunately, namnp who participated together failed to complete the demonstration within the specified time. As for the detailed vulnerability utilization report, the parties have not yet disclosed it.
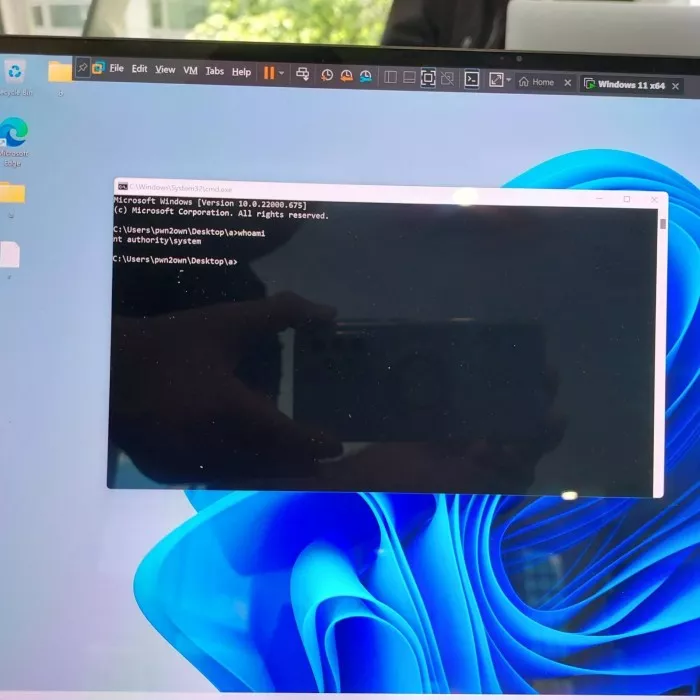
Finally, Bruno pujos of the reverse tactics team took advantage of the "use after free" vulnerability on Windows 11 to enhance privileges.
Interested friends, please also pay attention to the official follow-up war report.