After Microsoft announced the high-risk vulnerability of MSDT support diagnostic tool, another researcher exposed another zero day vulnerability of malware that can be connected to remote hosting The problem lies in the uniform resource identifier (URI) called "search MS", which can be used by related applications or links to enable the search function on client devices. Modern windows operating systems (such as 11 / 10 / 7) allow windows search to browse files on local and remote hosts.
Under normal circumstances, the user can set a URI with remote host and display name and display it on the title bar of the search window, while windows You can use various methods to invoke a personalized search window (such as running through a web browser, or win+r).
However, bleepingcomputer points out that people with ulterior motives or use protocol handlers to create fake windows update directories and then trick users into clicking on malware disguised as legitimate updates.
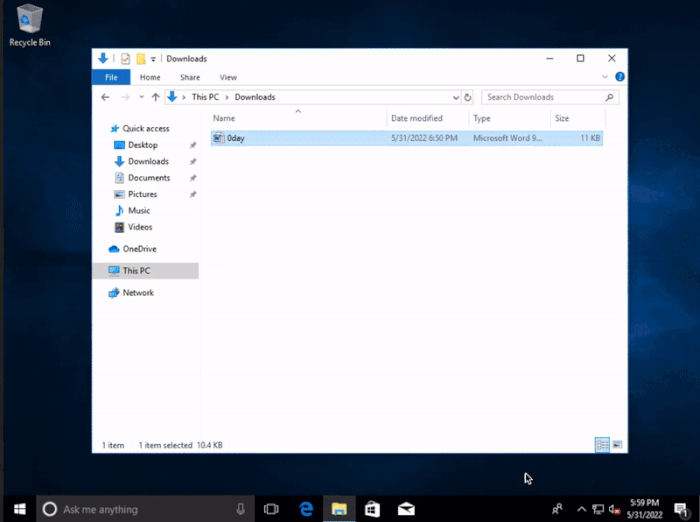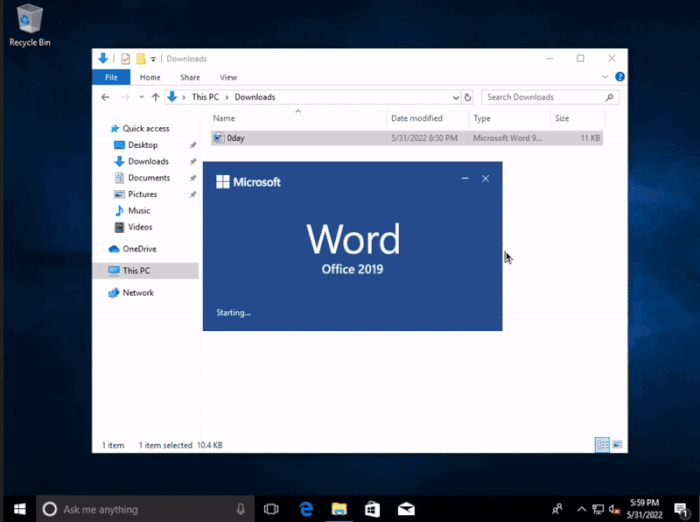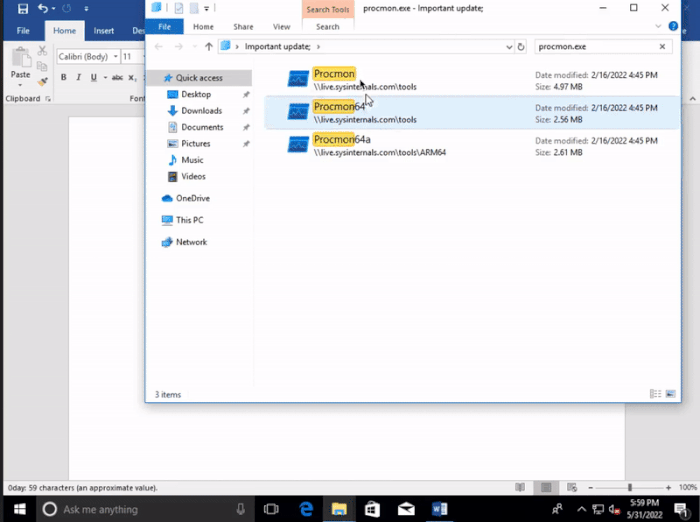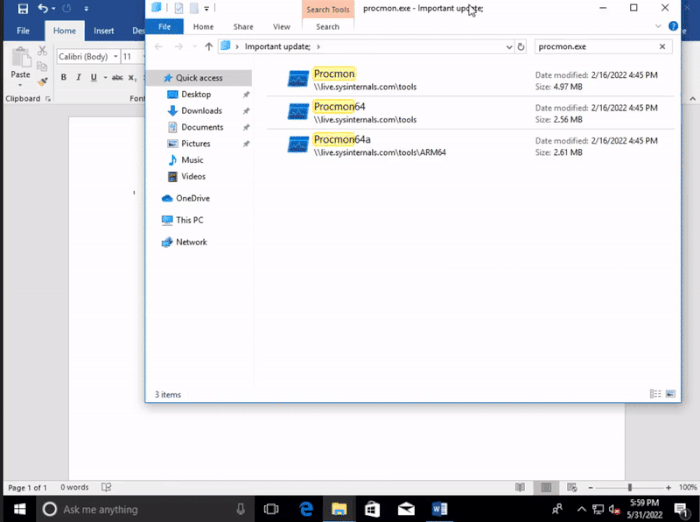
Fortunately, the search MS protocol vulnerability still requires the target user to perform some manual operations, and modern browsers (such as Microsoft edge) will pop up additional security warnings. Even so, the attacker can still use other "combination fists" to achieve his goal.
For example, in combination with Microsoft office A new flaw in oleobject allows you to bypass protected views and start URI protocol handlers without user interaction.
For the proof of concept, @hackerfantastic tried to create a word document that can automatically open the windows search window and connect to the remote SMB.
In addition, because search MS allows renaming the search window, hackers can even mislead users to take the bait through "personalized" search.
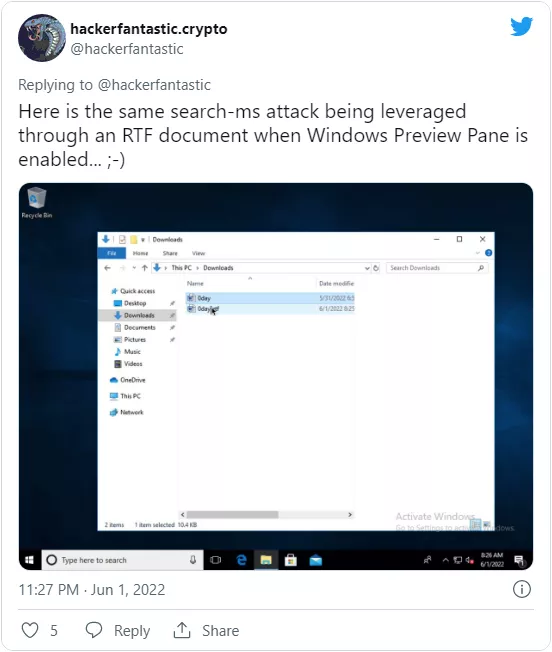
In another proof of concept, he even achieved the same goal through an RTF document, and this time he did not even need to start word.
The search MS vulnerability allows file explorer to automatically launch a new search window when it creates a preview on the preview pane.
To plug this vulnerability, the majority of modern windows operating system users (such as 11 / 10 / 7) can try the following mitigation measures:
● use the combination of winkey+r to call up the 'operation' window.
● press Ctrl + Shift + enter to run the CMD command prompt as an administrator.
● enter reg export HKEY_ CLASSES_ Rootsearch-ms search-ms.reg and execute to create a key backup.
● type reg delete HKEY_ CLASSES_ Root\search MS /f and confirm the execution to delete the key from the windows registry.
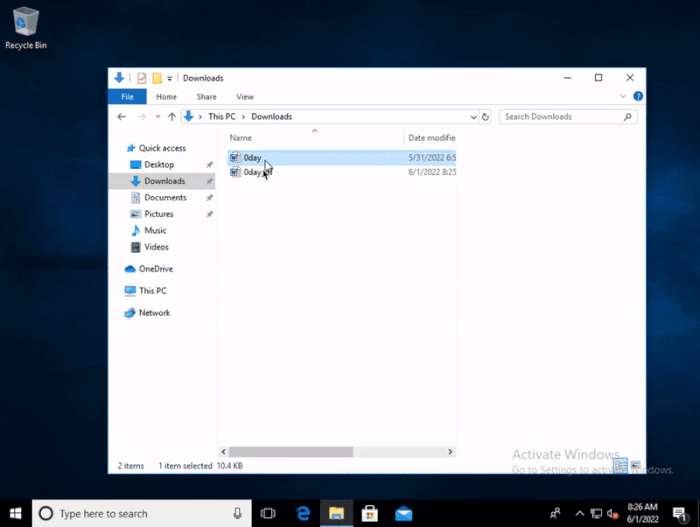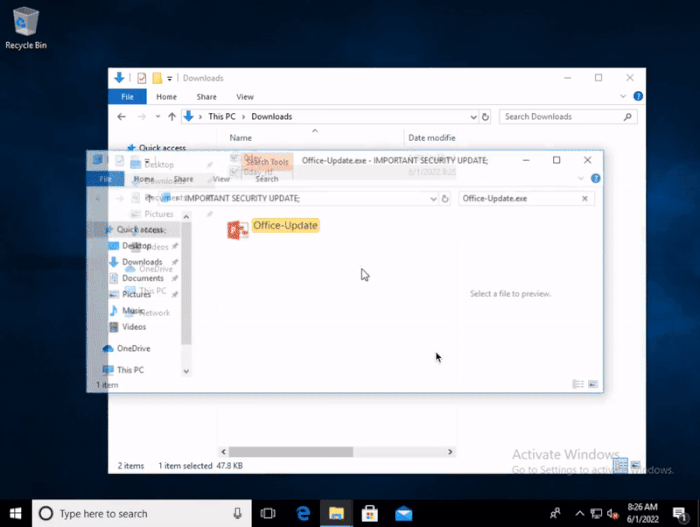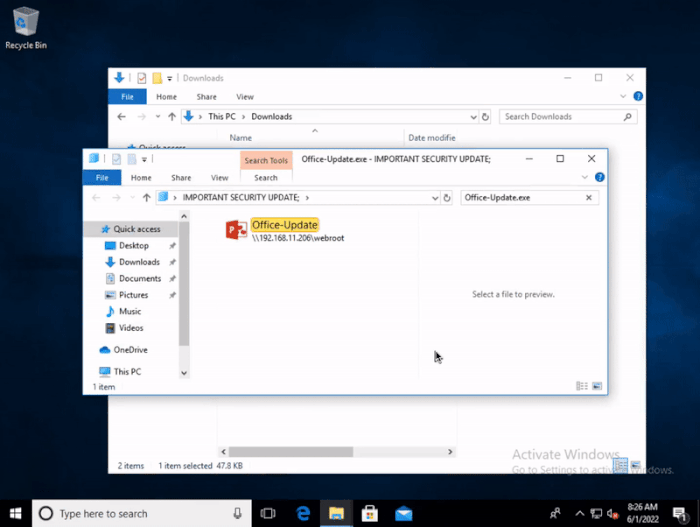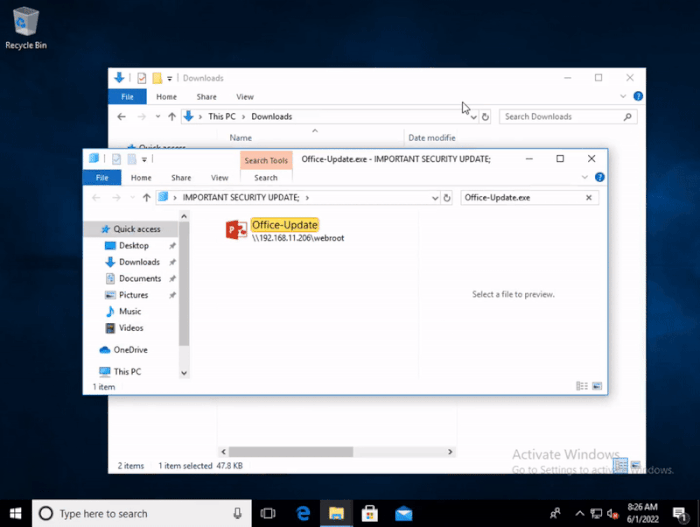
At present, Microsoft is trying to patch the vulnerabilities in the protocol handler and related windows functions. Even so, security experts still warn that hackers may find other exploitable combination defects at any time.
In view of this, we can only hope that Microsoft will focus on plugging the functional vulnerability that "office applications can be used to mobilize URI handlers without user interaction".
In fact, last year's printnightare vulnerability exploitation has been a lesson. However, Microsoft only fixed one component at that time, and later let researchers expose other vulnerabilities.