"God, is my money gone?" When logan Evans, a 24-year-old American boy, learned that his game axie infinity was involved in a hacker theft, his first reaction was "worried that he had lost everything".
Axie infinity is a world-famous NFT game, a typical gamefi (game Finance) product. According to axie's official website, the market turnover of the game has reached US $3.6 billion, attracting about 2 million users worldwide every day. The theft, with a loss of about $625 million, is the largest hacker attack in the field of defi (decentralized Finance).
Hackers have targeted the "fat meat" of encrypted currency. According to the data report released by chainalysis, hackers stole $3.2 billion worth of cryptocurrency in 2021. In the first three months of 2022, hackers stole $1.3 billion from exchanges, platforms and individuals, 97% of which came from the defi protocol.
The encryption world is facing an unprecedented crisis of trust and security challenges. Blockchain security deserves people's attention. If security and trust are not guaranteed, blockchain ecology will become empty talk.
In the blockchain world, new concepts and technologies continue to grow, but security has always been the foundation for building a new ecosystem.
Hackers focus on "cross chain bridge"
In addition to worrying about losing money, what makes players like Evans more dissatisfied is that the game company reacts on the 6th day after being attacked, or through user reminders. Players feel that the company's negligence is the worst of the whole thing.
In fact, the target of this hacker attack is not the axie game itself, but the cross chain bridge ronin bridge derived from it.
It's not unfair for the game project party to be criticized. Originally, each cryptocurrency runs on its own independent blockchain, and there is no simple way to interact with each other. For example, you can freely trade ether coins with different addresses on Ethereum, but you can't send ether coins directly to other chains.

Axie infinity game page| Source: NBC News
The ronin bridge attacked by hackers is the cross chain bridge created by the game company for axie ecology, which is convenient for players to send and exchange game tokens between different blockchains, bypassing the expensive transaction costs on Ethereum.
With ronin bridge, the cross chain transmission of funds that could not be realized has become "smooth" operation.
In the multi chain world, cross chain bridge is an important infrastructure, just like the Internet and road traffic in the real world. The cross chain bridge can connect different blockchain systems, allowing users to transfer and exchange tokens between different chains.
In short, the cross chain bridge can transfer assets from one blockchain to another, opening up the operation between different blockchain systems.
On the cross chain bridge, capital exchange is a very common thing. Axie game company is likely to mistake the hacker's operation for the user's normal deposit and withdrawal behavior. In addition, due to the lack of a complete contract balance monitoring system, the attack was not found at the first time.
Smart in business, stepped into the pit of technical safety.
Where's the stolen money
Evans was lucky that he didn't have real money loss due to hacker attack - he held the same amount of game currency as the original, but he couldn't withdraw money from the game for the time being.
But not all players are as lucky as him. After hackers attacked ronin bridge, they stole 173600 Eth and 25.5 million usdcs, worth US $625 million. Where did the stolen "money" go?
Wangpeiyu, a senior engineer of the blockchain security company certik (official account id:certikchina), told geek park that after the money was hacked, it all went to a wallet address of the attacker.
Every few days, the attacker will take some money out of his wallet and transfer it to mixer or tornado cash, a tool that can be considered as "money laundering".
As of May 4, Beijing time, almost all the stolen funds had been transferred, leaving only 1.8 eth in the original attack wallet.
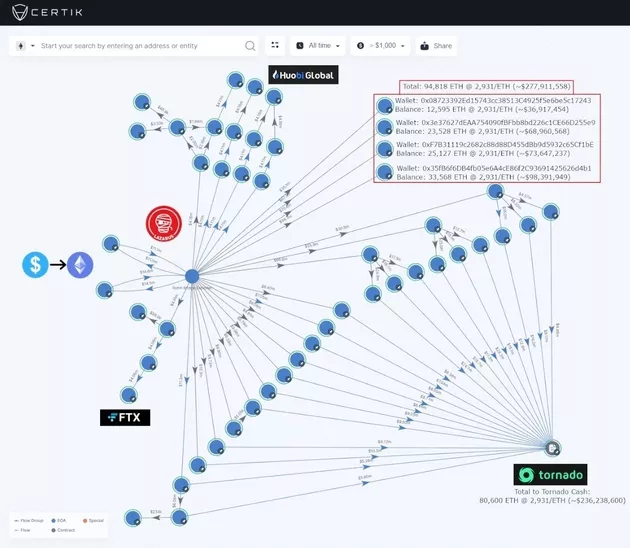
Certik uses skytrace to generate the latest stolen capital flow chart| Source: Twitter account @ certifikalert
Next, the attacker is likely to use other wallet addresses to withdraw money from tornado cash to complete the closed loop from theft to "money laundering".
The specific principle is as follows: Tornado cash is like a fund pool. Everyone can deposit money into the pool and then withdraw money from the pool with another wallet address. The system will provide a withdrawal password, which can be used by any wallet address to withdraw money.
The important point is that the wallet address for withdrawing money is anonymous, while the wallet for saving money can often find the source.
With the continuous maturity of on-line analysis technology and the authentication that some capital changes need to be filed with the exchange, the owner behind the wallet can be judged to a certain extent through on-line behavior. As a legal tool, tornado cash is intended to provide users with the function of protecting privacy.
Due to the huge amount of funds and the complex process of "money laundering", it is not easy for hackers to "wash" them all.
So, is it possible to recover the lost money?
If the amount of stolen funds is only one million, the possibility of recovery is very low. In the ronin Bridge incident, after the attacker deposited more than 600 million US dollars into the capital pool, the possible result is that a lot of money in the pool belongs to him. In this case, once a large withdrawal operation occurs, it is possible to judge whether the back of a withdrawal address points to the attacker.
In short, the more money is hacked, the more difficult it is for hackers to "wash" it in a short time, and the greater the possibility of recovery. However, it is difficult to say how much can be recovered.
Why do "injured" always cross the chain bridge
Ronin bridge was attacked because the verification node was lost. There are 9 authentication nodes on ronin bridge, and each node has a corresponding signature and private key. If the user wants to deposit and withdraw money successfully, he / she needs to provide at least 5 signatures among the 9 authentication nodes.
The attacker successfully invaded four verifiers and a third-party verifier of ronin bridge, obtained five legal signatures and won the funds on the cross chain bridge.
In the final analysis, there are loopholes in the management of private keys by game companies. In addition, the studio wanted to use multiple keys to authorize operations and improve the security of transactions, but did not revoke the access rights of the early list of game projects in time, which provided an opportunity for hackers.
This is not the first time that hackers have attacked the cross chain bridge.
Six months ago, the cross chain bridge named poly was hacked and lost about $600 million. At the beginning of this year, three similar "bridge bombing cases" occurred within 10 days, which aroused people's vigilance - "bridge" has become a weak link in blockchain security.
Even Ethereum co-founder V Shen publicly expressed his support for "Multi Chain" rather than "cross chain", opposed the use of cross chain solutions between Ethereum and other blockchains, and believed that cross chain bridges would increase security risks in the process of asset transfer.
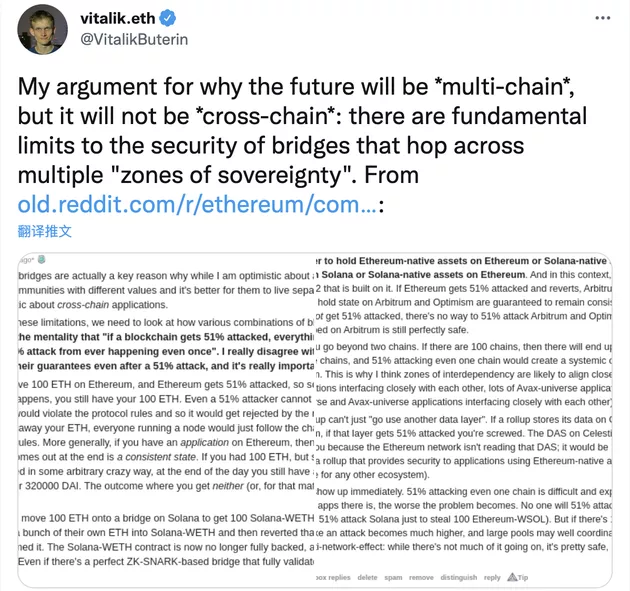
V God believes that there are basic safety restrictions on cross chain bridges| Source: screenshot of Twitter account @ vitalikbuterin
Cross chain bridge has become the weakness of blockchain security. We need to start with two concepts: on chain transaction and cross chain transaction.
Yang Yuannan, a certifik engineer, introduced that these are two completely different transactions. On chain transactions rely on the consensus mechanism of blockchain algorithm - its security has been verified by theory and practice. If the blockchain is regarded as a system, a separate transaction on the chain only updates the data in the system to reach a consensus.
Cross chain transactions are not. The word "cross" breaks the barriers between blockchains, which also means that different systems at both ends of the "bridge" need to be updated to a certain extent, and there may be great differences between the two systems. Because the design of each chain can only ensure the transactions on the chain, cross chain transactions need to rely on many additional mechanisms, such as monitoring, processing and sending the information on the chain, which is much more complex and difficult than the transactions on the chain.
For example, it is convenient and easy to transfer money in the same bank, but if you want to transfer money to other banks or even overseas banks, not only the process is complex, but also the handling fee.
The role of cross chain bridge is to ensure the correctness and consistency of capital changes between two different systems.
For example, to transfer 10 eth on Ethereum to the money security chain, the cross chain transaction process roughly includes:
After receiving 10 eth, the bridge contract at Ethereum will release a transfer message;
The cross chain network listens to this message;
The cross chain network calls the bridge contract at the end of the coin security chain to provide the user with coins equivalent to 10 eth.
The whole process involves three interrelated but relatively independent individuals: Bridge contract on Ethereum, cross chain network and Bridge contract on money security chain. They are on different platforms, and they only ensure the transmission of data between chains through message passing mechanism.
Cross chain project itself is a complex system, and the core here is the message passing mechanism. Once there are loopholes in this mechanism, it may become the key for hackers to forge cross chain messages and launch attacks.
It is difficult to verify the security of cross chain operation, and because the server responsible for monitoring messages is not in any blockchain system, it can only restore the operation instructions through the monitored messages and the preset message format. In this way, the accuracy of restoration depends on the correctness of the series of processes of publishing messages, listening and decoding, which is difficult to be verified.
In addition, the code complexity of different cross chain projects is high, the differences are large, and the potential security problems are more diversified. Compared with assets stored only on a single chain, assets involved in cross chain networks are more unstable and easier to lose.
The reason why the cross chain bridge is complex is that the two sides of the cross chain are completely different systems. As an intermediate third party, the cross chain network has potential risks in its message processing ability, message verification and issuance security.
Although the "bridge" has increased the security risk in the process of asset transfer, cross chain projects are still emerging in large numbers. The funds active on the "bridge" are like cakes on a static plate. They are delicious and easy to take, attracting hackers to attack one after another.
(geek Park)
Ronin bridge was hacked and taught another lesson to the project parties: to avoid hacker attacks, the most important thing is to ensure the security of the private key. In terms of specific implementation, hardware wallets with higher security can be used; Ensure the dispersion of multiple private keys; Revoke the permission of an abandoned node in time.
The coat of web 3, the soul of Web 2
In people's imagination, security is one of the inherent characteristics of the "decentralized" blockchain and web 3 world. Unexpectedly, it is not a problem.
This is not only the result of multi factor game, but also an economic account. In terms of design, the cross chain bridge can be decentralized or centralized, but the design cost and operation cost of decentralization are higher than centralization because it is more complex.
As mentioned above, the transfer of assets on a decentralized bridge requires the signature of multiple nodes, which can only be realized by relying on complex design and resource investment. If the centralized bridge is replaced, the design and management of the project party will be more convenient and the cost will be lower. Some cross chain projects adopt a centralized information processing method for the efficiency and convenience of the system.
Some people think that the centralized bridge deviates from the spirit of web 3, and behind it is a set of old logic of Web 2.
However, in Wang Peiyu's view, the existence of cross chain bridge is still closer to web 3, which is a typical product of web 3. Because the function of cross chain bridge is to transfer money from one blockchain to another, which is realized on the bridge. Almost all bridge implementations include the logic of smart contract, which is the code existing on the blockchain.
The boundary between centralization and decentralization is not clear-cut. There is a "centralization risk" in the world of web 3.
Hacking incidents occur frequently. One reason is that security vulnerabilities are buried in the preparation of smart contracts. Another reason is that there are logical vulnerabilities in the design of the defi project. For example, the impact of adding handling charges on the transaction logic is not taken into account.
For defi, "centralization risk" usually comes from the existence of privileged accounts in a project. Privileged accounts can change the configuration of smart contracts at will, and even use the funds of other ordinary users, which has the risk of transferring funds.
When the privileged account makes mistakes in updating the configuration, it will also cause losses to other users.
Privileged accounts have too much power and may also provide hackers with a free access permit. Once hackers have captured the private key of the privileged account, they may steal project funds through this account and damage the rights and interests of others.
The birth of cross chain technology and projects has broken through the barriers between different blockchains in the encryption world and can improve the Economic Liquidity of virtual currency. Gamefi products represented by axie enrich the application scenarios of blockchain, make the technology more people-friendly and reduce the participation threshold of web 3.
But it is worth being vigilant that there is no invariable beauty. Just like the real world, there is often a crisis hidden in places with interests. The greater the interests are, the more complex the crisis is.
The blackout of ronin bridge does remind krypton gold players like Evans, but he doesn't intend to give up the game. "I still believe in axie and I love everything in this community."
Author Xue Xiaowan
Editor | Jingyu
reference material:
https://www.nbcnews.com/tech/crypto/axie-infinity-hack-leaves-players-shaken-still-loyal-rcna23379
https://www.theverge.com/23017107/crypto-billion-dollar-bridge-hack-decentralized-finance
https://blog.chainalysis.com/reports/2022-defi-hacks/