Tesla has been exposed to security risks again?? The problem this time is the "keyless entry system". A network security officer found that through relay attack, it only takes 10 seconds to unlock a model 3 or model y. This method is not difficult to operate. Just put equipment on the owner's mobile phone (key card) and near the vehicle, and you can disguise as the owner to open the door and drive away the vehicle. The total cost of the technical software and hardware used is about 1000 yuan, which can be bought online.
At present, network security personnel have reported this vulnerability with Tesla. No case has been found of anyone using this method to steal Tesla.
1000 yuan can invade a Tesla
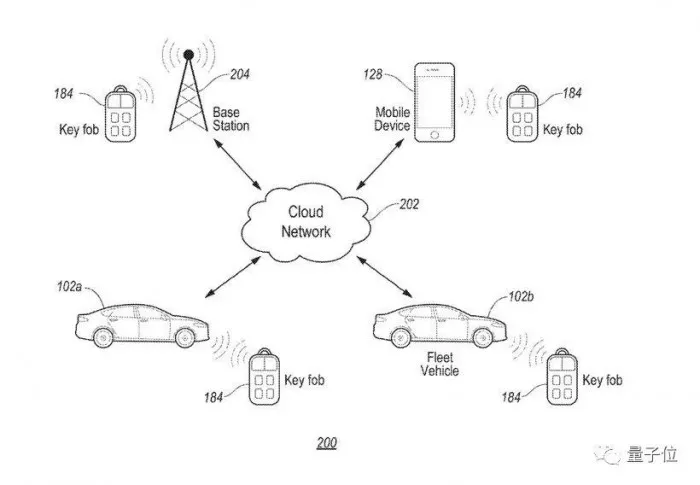
This crack is mainly aimed at Bluetooth low power consumption (ble) used by keyless entry system.
This is one of Bluetooth technology, which is characterized by ultra-low power consumption, low cost and short distance use. It is commonly used in intelligent devices of the Internet of things, such as smart door locks, smart appliances, anti loss devices, health bracelets, etc. Compared with the classic Bluetooth, it is more suitable for transmitting small amount of data, such as transmitting the monitored heart rate and blood pressure value to the mobile phone.
Tesla keyless entry system also uses ble to let the mobile phone or key card communicate with the vehicle.
Using this principle, network security personnel can complete the cracking by using relay attack.
In this method, a decoding sensing device needs to be close to the owner's mobile phone or key card, collect the corresponding digital password and transmit it to the receiving device next to the car. At this time, the vehicle will mistakenly think that the receiving device is the key, and the door can be opened after simple operation.

According to the network security personnel, this attack method requires the use of Bluetooth to develop the code of the kit, which can be bought online for $50 (about 338 yuan). The hardware equipment used can also be bought online for about $100 (about 677 yuan).
The network security personnel who found the vulnerability have disclosed the problem to Tesla, but the staff said that this does not pose a major risk. And this method is not limited to attacking Tesla cars.
In 2019, a British survey found that more than 200 models were vulnerable to such attacks. Even the smart lock used on the door can be opened in this way. Therefore, many manufacturers have come up with countermeasures. For example, Ford has just applied for a patent for the vehicle key card relay attack prevention system.
This is a new identity authentication system, which can judge whether the original key is near the vehicle, so as to block the relay attack.
The method used in modern cars is to keep the keyless entry system in sleep mode when the equipment is stationary, so as to prevent the transmission of radio signals. There are also key boxes on the market that can cut off the signal, but this method is not suitable for mobile phone unlocking.
In addition to automobile manufacturers, some manufacturers will use dual identity authentication systems, such as Kwikset Corp. KEVO, a smart door lock company. They said that using iPhone This method can be used to prevent intrusion when unlocking, and the iPhone operation has a 30 second time limit, which can also prevent hackers from cracking.
As for Android users, there will be a system upgrade to solve this problem in the future.
One More Thing
Tesla was exposed security vulnerabilities is not new.
At the beginning of this year, a 19-year-old German boy used program loopholes to crack 25 Tesla cars in a row. It can remotely control doors and windows, lights, music and even drive away.
However, this vulnerability is not in Tesla system, but in third-party software.
Previously, there were defects in the software of model s, which may lead to hackers turning off the engine system when the car is moving.
In 2020, model X was exposed, and the autopilot was hacked many times.
And researchers from the University of Leuven in Belgium demonstrated how to "steal" a model X in 90 seconds.
They used raspberry pie DIY to buy a car key. Using the loophole of Tesla key, they can "copy" the original key near the owner (within 15 meters). It can not only open the door, but also start the on-board system.
Obviously, the safety of Internet connected vehicles needs to be further strengthened
What do you think of this?
Reference link: