I didn't expect that the computer term "Ping" was discussed and searched under the topic of MSI of hero League. Whether on Weibo or Zhihu, many "Ping" related topics have been hot for tens of millions or even hundreds of millions. From the discussion under the topic, many netizens even have a passion for Ping research:
Speaking of, the little friends who often play online games must be familiar with Ping. Who hasn't felt the fear of being dominated by Ping several times? (manual dog head)

△ high Ping soldiers are fearless
The higher the Ping value, the higher the network delay when playing the game. In the game, people with low delay make all kinds of actions (killing, moving, etc.) faster than those with high delay.

Note that the Ping value here does not represent your network speed.
Let's put it this way. If your packet is an express delivery, the higher the Internet speed, the greater the truck tonnage, and the Ping value represents how fast the truck can run and how congested the road is.
The lower the Ping value, the smoother your network is, but it has nothing to do with how much data it can carry at a time.
But do you know how Ping was first invented? In fact, this "ubiquitous" computer technology in playing games, meetings and measuring delays was written "casually" in those days. The story will start in the 1980s.
Thousand lines of code from 1983
This tool called Ping was originally developed by a brother named Michael John muuss.

Muuss was born in 1958. After graduating from Johns Hopkins University, he did research in a weapon test center called "Aberdeen test field" of the U.S. Army, mainly related to computer network and geometric modeling.
For example, when ray tracing became popular in the 1980s, brother muuse was already studying the corresponding technology. During this period, he made a lot of relevant achievements, but instead, Ping was "invented" and has now become one of the most famous network tools .
To what extent is Ping widely used? From the original UNIX system to today's windows , MacOS and Linux, Ping has been widely used on various operating systems , although it has gone through several versions.
Now we can find a lot of code to realize Ping on GitHub, but these are not the original versions.
Muuss provided the original source code of Ping on its home page. However, when we click in, we will find that the web page jumps several times and finally seems unable to download:

In fact, we can also see muuss's homepage, which is already unusual in itself - muuss died in a car accident in 2000, just after his 42nd birthday:

Fortunately, the web page at that time was saved on the Web Archive, and we were able to see the first version of the source code of Ping.
The code file name is Ping Shar, a very age-old suffix, is now almost no one uses this file extension. It is a 41KB file. From the editor, there are about 1600 lines of code:
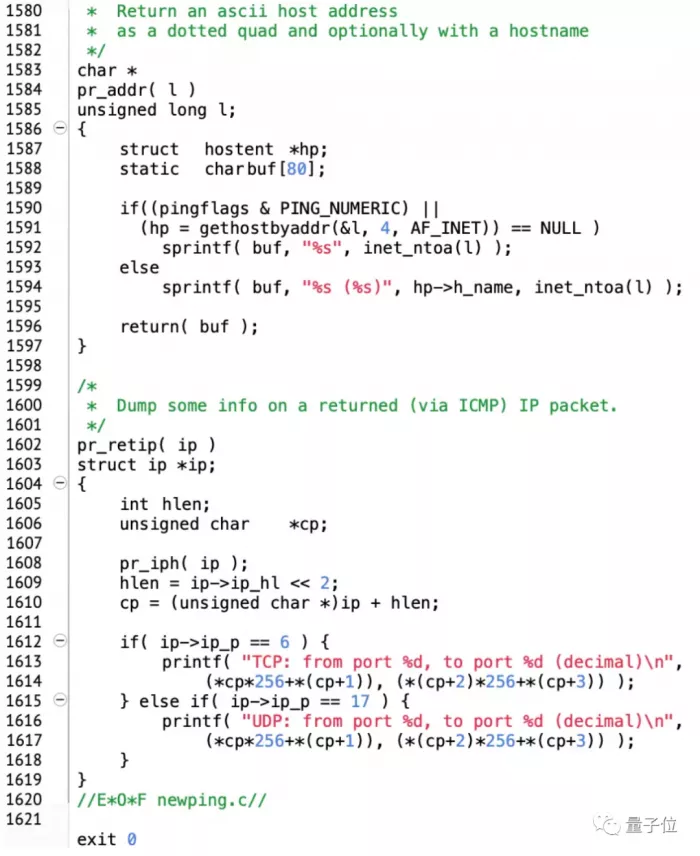
So, how was Ping born and popularized?
How was Ping popularized?
When he first wrote this code, muuss had no idea that it would become so popular later. After all, the initial Ping was just a test tool for troubleshooting laboratory network abnormalities.
One day in December 1983, when muuss was doing experiments in the trajectory Research Laboratory (BRL) of Aberdeen Proving Ground, he suddenly found that the IP network of the laboratory was abnormal.
At this time, he recalled that a few months ago, he had participated in a seminar held by DARPA in Norway. At the seminar, a doctor named Dave mills mentioned the method of testing delay with ICMP packets.
Muuss believes that the principle of this tool is like transmitting sound waves and receiving its echoes to calculate the round-trip time .
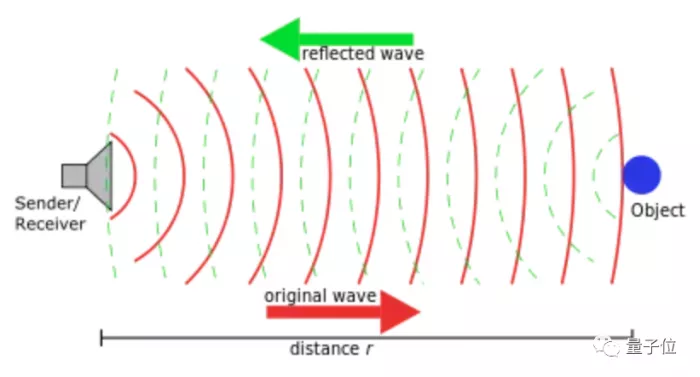
△ sonar, source Wikipedia
It happened that muuss learned a lot of modeling of sonar and radar system in college. He quickly wrote a program and named it Ping , in sonar, it refers to sound pulse, that is, signal . Then, it took muuss only one night to write the ping program.
Although his lab had solved the network problem when it was written, muuss released it as a public domain software (no license required for use).
Soon Eric engelke of the University of California, Berkeley, discovered the software and rewritten it into a version (following the GPL open source protocol) into Berkeley's own UNIX operating system bsd4 In version 3.
Subsequently, computer engineer Tim Crawford wrote a ping code of ReactOS version based on MIT open source protocol. After that, Ping was written into various operating systems, such as MacOS, Linux and windows, and more functions were added.
△ Ping on Linux system c
The Ping tools we see in each system are not the original Ping Shar program, its functions and usage are much richer. What is Ping on a computer today?
Basic principle of Ping
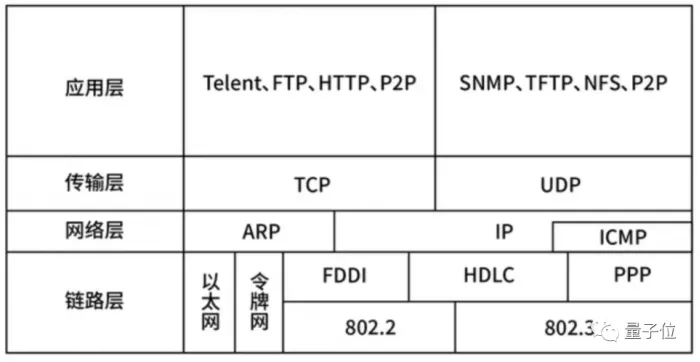
Many computer enthusiasts may say that they Ping too much. But do you know how Ping works? Ping is a network management command in the application layer of the network structure and an important means to judge whether the network between two hosts or routing nodes is unblocked.
To put it simply: if the two hosts are "Ping", it means that a connection can be established between them.
A little knowledge: the IP address of the public network (Internet) is unique. This is like working in a building (host or routing node, etc.) in the world (public network). The address (IP address) of this building is unique relative to the world, but other house numbers (intranet IP address) in the building are not necessarily unique.
Using this feature, we can ping the network connectivity between two hosts or routing nodes. Specifically, use the ping command to send an ICMP compliant packet (echo request) to the target IP address first. Then you can check the network status between hosts or routing nodes according to the returned packets (packet loss, speed, etc.).
EMM... What is ICMP Protocol? Its full name is: Internet control message protocol, that is, Internet control message protocol. ICMP message is encapsulated in IP packet. The so-called "control" refers to the transmission of control messages between IP hosts and routing nodes to reflect whether data packets successfully reach the target end and network conditions.
In IP communication, when the IP packet successfully reaches the destination address and returns, it will receive a ping response; When the IP packet fails to reach the target address or return from the target address for some reason, the data packet returned by ICMP will contain specific reasons, such as network unreachable, port unreachable, etc.
How to Ping up
The following describes the basic operation of Ping. The ping command is common in all common operating systems. Here, take MacOS as an example: find the "terminal" in the finder.

Enter Ping + IP address (web address or domain name can also be used). Here, take Baidu as an example. Then, you can view each data packet and the delay time from the computer sending data to Baidu's network server to receiving the feedback data from the server.
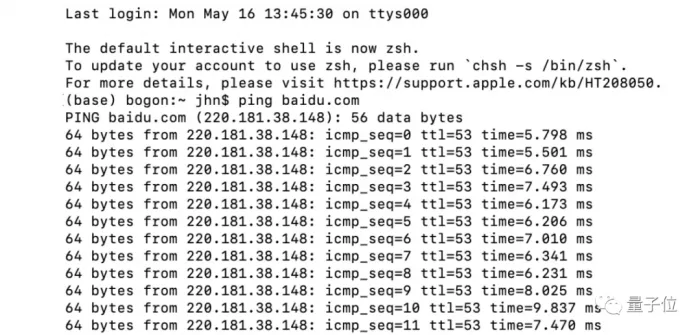
Since the default size of each IP packet sent by MacOS is 64 bytes, the returned packet size is also 64 bytes.
The delay time here is the Ping value. In addition to entering Baidu and other websites, there is no problem to test the Ping value between two hosts. Just enter the IP address of the other on one host:
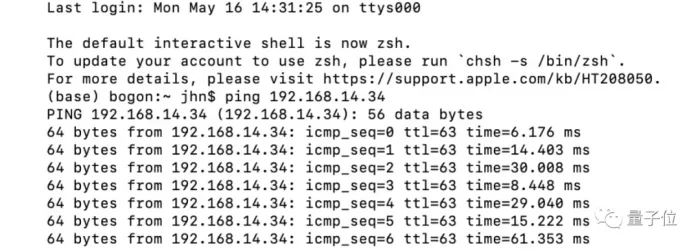
Therefore, when playing online games, if the Ping value is too high, it will feel the operation delay. The consequences of this delay are quite serious - for example, at the critical moment of the king's ranking, if the network connection (which may be your own wireless network or a nearby server) gets stuck, it is clear that you have operated, but because the enemy's operation feedback time is faster, you can only watch your hero die.

At this point, qubit hurried on the number and diagnosed its own network.
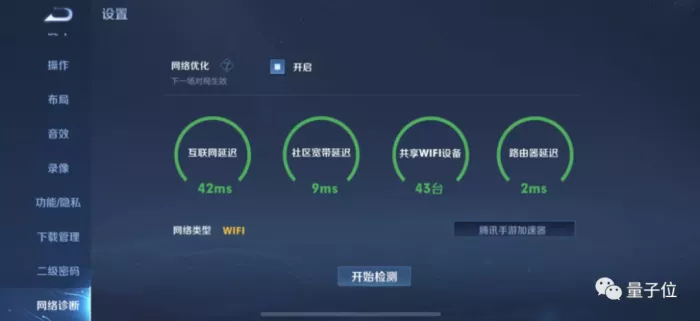
Fortunately, the delay of King glory is less than 70ms, which is normal. For lol, players can open the setting menu, click the "display" tab, and then click the "switch FPS display" button to view their own Ping value.

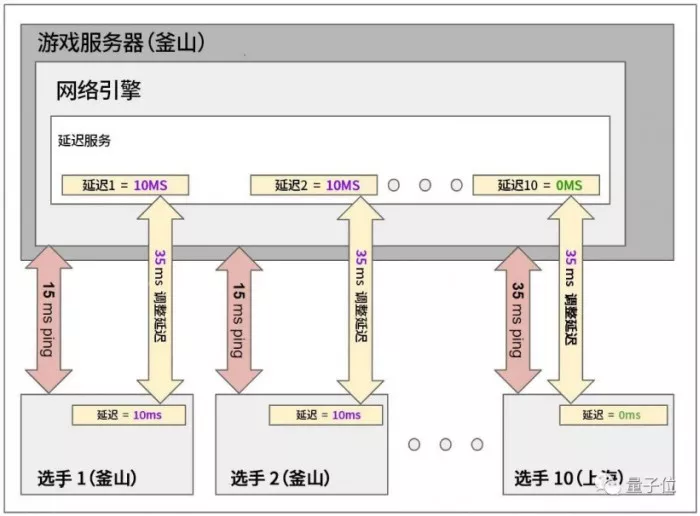
As for how to realize the lock Ping (manual delay) technology, the fist game official has given a technical description:
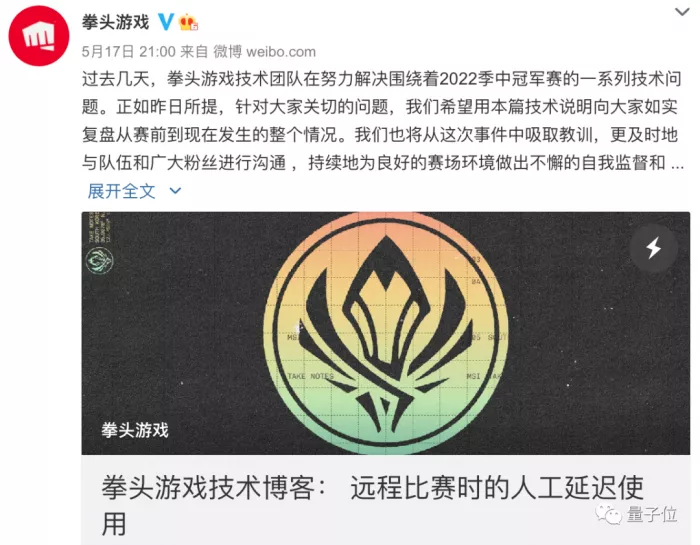
From the description, fist means that a manual delay tool is added to adjust the Ping value during the next online competition. Due to the error in the code operation of the manual delay tool, the offline Ping value is too high. At present, it has been repaired by adjusting the configuration, but the Ping value displayed in the game will have problems due to this configuration adjustment .
The technical code of the specific manual delay tool (lock Ping) is not disclosed in the fist game at present. However, some people have made artificial delay tools on GitHub, such as the following clumsy open source simulator, which can simulate delays, packet loss and other bugs. Interested partners can go and have a look:
One More Thing
On his home page, Muse also Po posted another interesting story related to "Ping". As early as 1933, American children's picture book writer Marjorie flack once published a picture book: "the story of Ping".

Here, Ping is the name of the story protagonist duckling: duckling Ping lives in a boat with his partner and owner. The last duckling to go home every day will be spanked. One evening, Ping greedy fell at the end. In order not to be beaten, he didn't go home, so he started a wonderful adventure in the Yangtze River and finally returned to his master's ship safely.
This seems to be an ordinary children's book, but many years later, some readers found that the story of duckling Ping is similar to the Ping packet in the computer! A Ping packet is like a duck. It spends a period of time on the host (boat) together with other packets (more ducks).
Then, these data packets (ducks) leave the host (ship) through a channel (bridge) and enter the Internet (Yangtze River). The data packet (duck) returns to the original host (ship) after a short time on another host (ship). So, what's your Ping value today?
Reference link:
[1]https://blog.paessler.com/a-brief-history-of-ping
[2]https://ftp.arl.army.mil/~mike/ping.html
[3]https://s.weibo.com/weibo?q=%23MSI%E7%8E%B0%E5%9C%BA%E5%AE%9E%E9%99%85ping%E5%80%BC%23
[4]https://github.com/iputils/iputils/blob/master/ping/ping.c
[5]https://en.wikipedia.org/wiki/Mike_Muuss
[6]https://ngabbs.com/read.php?tid=30095855&;rand=196
[7]https://github.com/jagt/clumsy
[8 ] fist technology blog announcement: https://weibo.com/ ttarticle / p / show? id=2309404770219460790187