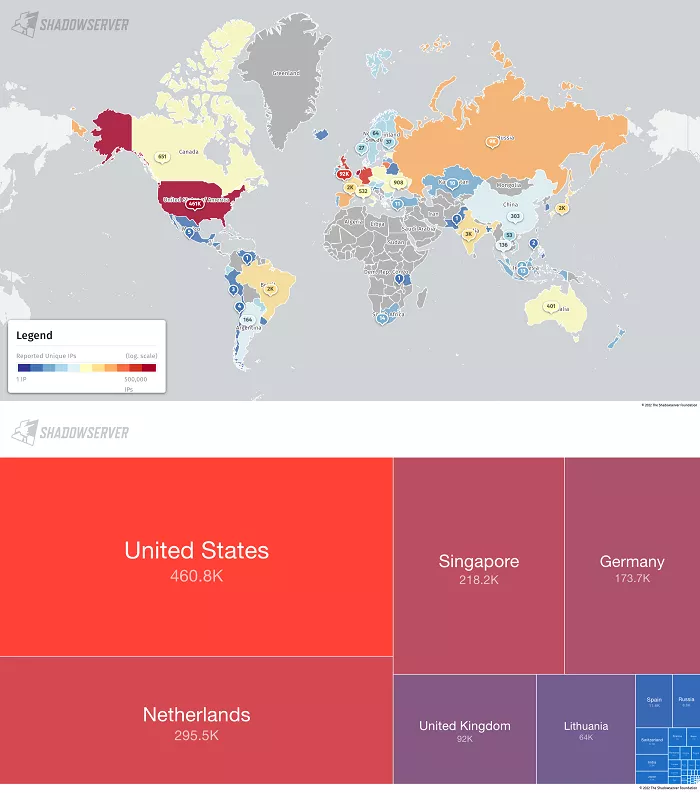
The network security research organization shadowserver foundation scanned last week and found that nearly 3.6 million MySQL servers on the Internet are using the default TCP port 3306 The report states that although it did not analyze the access level / exposure of the database in depth, this potential attack surface could have been easily evaded. From a regional perspective, the United States ranks first with 1.2 million plus, followed by China, Germany, Singapore, the Netherlands and Poland.
IPv6 connection distribution (from: shadow server)
Bleeping Computer It is pointed out that more than 3.6 million MySQL servers exposed to the Internet will publicly respond to queries, making them attractive targets for hackers and blackmailers.
In addition, among these accessible MySQL services, 2.3 million devices are based on IPv4 connection, and another 1.3 million devices adopt IPv6 connection.
Although it is common for web servers and applications to connect to remote databases, in reasonable security practice, the relevant instances should be locked to allow only authorized devices to connect.
Even if it has to be exposed to the Internet, the server side should always be accompanied by strict user policies, modifying the default access port (3306), enabling binary logging, and closely monitoring all queries and implementing encryption.
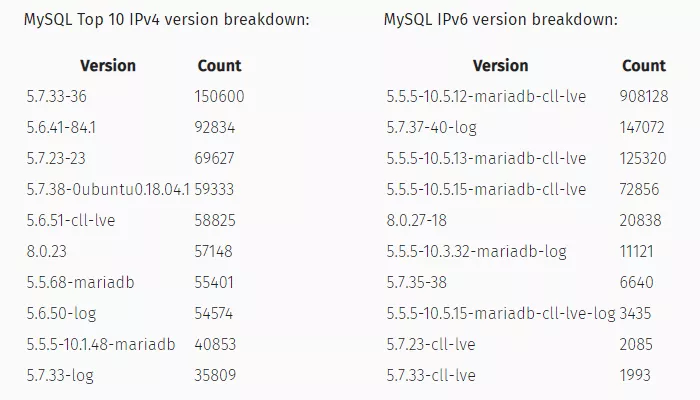
MySQL version distribution
The detailed scanning results are as follows:
● total IPv4 exposure: 3.957457 servers
● total IPv6 exposure: 1421010 servers
● total number of IPv4 server query responses: 2.279908 times
● total IPv6 server query responses: 1343993 times
● in addition, nearly 67% of all exposed MySQL servers can be accessed through the Internet.
It is reported that one of the common sources of data theft is various databases with improper security. The administrator should always lock the database to prevent any unauthorized remote access.
In addition to catastrophic data leakage, the database server with incorrect configuration may also be subject to destructive attacks, ransomware / remote access Trojan (rat) infection, or even cobalt strike attacks.
To learn how to deploy MySQL server safely and eliminate potential system security vulnerabilities, shadow server recommends that administrators read 5.7 / 8.0 Version of the implementation guide.