Jason donenfeld, a security researcher known for leading the development of wireguard open source software, recently outlined a security vulnerability affecting Oracle VM VirtualBox software. When SIMD registers are used in interrupt handlers, VirtualBox may leak data from the host to the client virtual machine.
Donenfeld explained in the kernel mailing list:
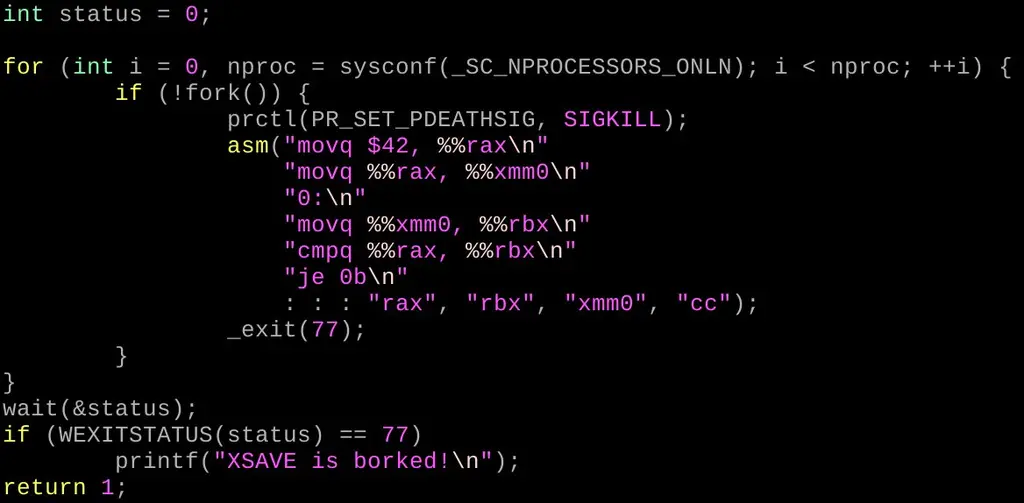
I wrote a small reproduction to test this problem. It should be quite reliable. I think it proves my work theory. Run this in the VirtualBox virtual machine, then move your mouse or hit the keyboard, or do some add to trigger the hardirq processor_ {input,disk}_ Randomness () path. For example, on my laptop, track points are made through hardirq, but the touch pad is not. As long as I move the track point, the following program will print out "xsave is borked!".
In addition, please note that this is not only the "damage" of the guest virtual machine, but also divulges the secret content of the host virtual machine to the guest. So you may really want to ensure that VirtualBox releases a fix before 5.18, because it can be said to be security sensitive.
This occurred in a series of patches around preventing FPU state corruption, which originated from recent random code changes. In addition, at the beginning of this month, the VirtualBox maintainer of openSUSE did not notice the kernel thread that Linux 5.18 crashed in the VirtualBox virtual machine.
VirtualBox hasn't fixed this problem yet, and Linux developer Thomas gleixner added in this series:
The virtualborx bug must be fixed in any case, because this problem always exists, and there have been sporadic cases of drivers using FPU in the context of hard interrupt in the past. Therefore, it is entirely luck that this problem has not been exposed before. Over the years, afaict has moved all this to the softirq context, so random code may be the only hard interrupt user in mainline today.
For the benefit of users, we should probably clench our teeth and prohibit the use of hard interrupt FPU in the upstream and CC stable areas. Stable kernel updates may reach users faster.